The CIA Triad In Architectural Design
The CIA Triad, consisting of Confidentiality, Integrity, and Availability, is a foundational framework in the realm of information security. Now it's time to explore how these principles can be seamlessly woven into the fabric of architectural design to create spaces that not only inspire but also protect.
George EvansFeb 15, 2024290 Shares17083 Views

The CIA Triad, consisting of Confidentiality, Integrity, and Availability, is a foundational framework in the realm of information security. Now it's time to explore how these principles can be seamlessly woven into the fabric of architectural design to create spaces that not only inspire but also protect.
Why The Central Intelligence Agency (CIA) Takes Interest In Information Security
The Central Intelligence Agency (CIA) stands as one of the United States' premier intelligence agencies, tasked with safeguarding national security interests and acquiring vital intelligence critical to the country's well-being. While traditionally associated with espionage and covert operations, the CIA's concern extends beyond physical realms to the intricate landscape of information security.
Why Information Security Matters To The CIA
- National Security Implications:Information security is integral to national security. The CIA is entrusted with protecting critical intelligence, and any breach could compromise the nation's safety. By upholding the principles of the CIA Triad, the agency safeguards sensitive data from adversaries seeking to exploit vulnerabilities.
- Counterintelligence and Espionage:Given its role in counterintelligence, the CIA is acutely aware of the constant threats of espionage and cyber-attacks. Ensuring the confidentiality, integrity, and availability of its own information is paramount to thwarting external threats and maintaining operational efficacy.
- Global Cyber Landscape:In an era dominated by digital interconnectedness, the CIA recognizes the significance of information security in the global cyber landscape. The agency's operations, communications, and intelligence-gathering efforts rely heavily on secure and resilient information systems.
For the CIA, the intersection of national security and information security is a critical nexus. A breach in information security not only jeopardizes classified intelligence but also compromises the effectiveness of the agency in fulfilling its mission. The CIA's commitment to the principles of the CIA Triad reflects a broader dedication to upholding the integrity and security of the nation's intelligence apparatus.
The Pitfalls Of Post-Development Security
Often, security measures are added hastily during the later stages of development or even after the launch of an IT project, resulting in potential risks and oversights. This reactive approach leads to a scattered array of security solutions, creating inefficiencies, escalating costs, and leaving organizations susceptible to emerging threats.
The Need For A Unified Information Security Architecture
In the ever-evolving landscape of IT projects, the imperative for a unified information security architecture emerges as a guiding principle. Rather than embarking on the quest for disparate security solutions for each new endeavor, organizations are better served by harnessing the potency of their existing information security architecture. This approach, rooted in strategic wisdom, not only promotes cohesion but also aligns security services harmoniously with core information security principles. The result is a seamlessly integrated and strategically deployable security framework that transcends individual projects, fostering a unified front against evolving cyber threats.
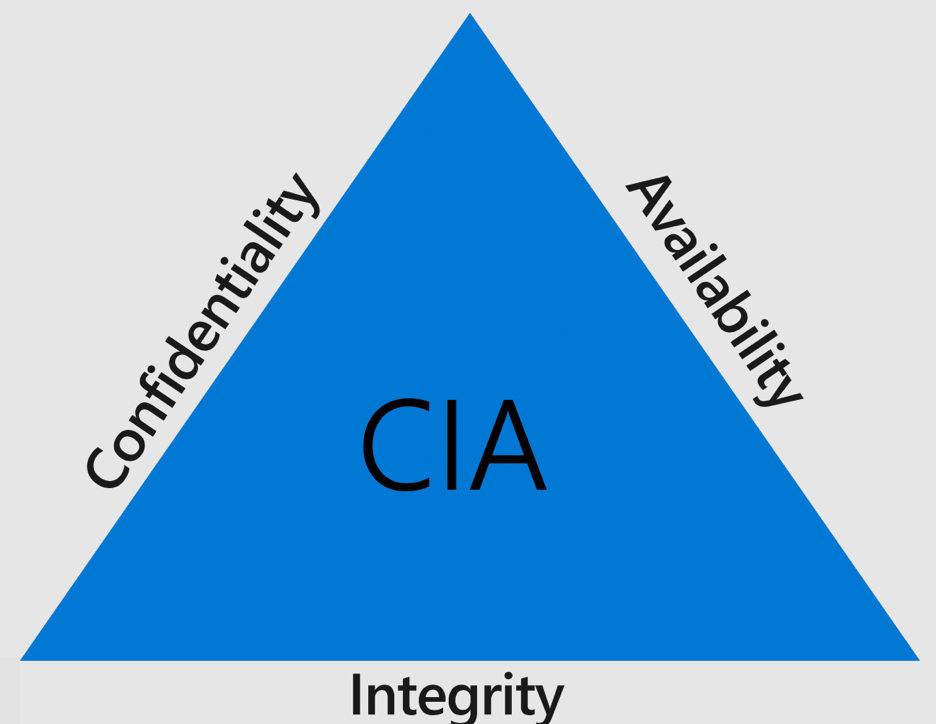
The CIA Triad - Core Principles In Information Security
Confidentiality
The first pillar of the CIA Triad revolves around maintaining the confidentiality of sensitive information. Privacyand secure data handling are paramount. Establishing information security policies should involve classifying data based on sensitivity, implementing protective measures, and managing access levels accordingly.
Integrity
Integrity focuses on safeguarding information from unauthorized modifications or deletions. It also emphasizes the ability to revert authorized changes made in error. Implementing this principle involves defining user roles, setting access permissions, and incorporating recovery systems to restore data in case of inadvertent changes.
Availability
Ensuring data is readily available for authorized users while preventing access by unauthorized individuals is the essence of the availability principle. Information security measures should facilitate seamless authorized access, even during incidents like DDoS attacks or power outages, ensuring business continuity.
Beyond The CIA Triad - Additional Considerations
While the CIA Triad provides a foundational framework, other critical aspects, including governance, user management, access control, and network security, must not be overlooked. These elements complement the triad, contributing to a comprehensive and secure network architecture.
Governance
Governance acts as the guiding force that shapes and directs information security policies. Establishing a robust governance framework involves defining roles, responsibilities, and decision-making processes. Effective governance ensures that security measures align with organizational objectives and industry best practices.
User Management
User management extends beyond access permissions. It involves comprehensive strategies for user authentication, authorization, and accountability. By implementing secure user management practices, organizations can mitigate the risk of unauthorized access and enhance overall system security.
Access Control
While the CIA Triad touches upon access levels, a deeper exploration into access control involves the implementation of multifaceted strategies. This includes role-based access control (RBAC), attribute-based access control(ABAC), and continuous monitoring to adapt access privileges dynamically based on changing circumstances.
Network Security
Network security serves as the backbone of a secure architecture. Beyond the CIA Triad, organizations must consider robust measures such as firewalls, intrusion detection and prevention systems, secure network design, and encryption protocols. These elements collectively fortify the perimeter and internal layers of the network against evolving cyber threats.
Real-world Applications
In the realm of architecture, the principles of the CIA Triad—Confidentiality, Integrity, and Availability—are not confined to the digital domain. They find tangible expression in the design and construction of physical structures, ensuring that the spaces we inhabit are not only aesthetically pleasing but also fortified against potential threats.
About Confidentiality
In residential architecture, the concept of confidentiality aligns with the creation of private spaces within a home. Architects strategically design bedrooms, private offices, and secluded corners to safeguard personal activities from the prying eyes of others. This design approach ensures that individuals can enjoy a sense of confidentiality within their own living spaces.
About Integrity
Integrity in architectural design mirrors the structural resilience of a building. Engineers and architects collaborate to ensure that buildings withstand external forces such as earthquakes or extreme weather events. By integrating robust materials and construction techniques, architects uphold the integrity of structures, preventing unauthorized modifications to the building's intended form and function.
About Availability
In public buildings, availability takes center stage. Architects meticulously plan layouts, entry points, and emergency exits to balance accessibility for authorized users with restrictions to prevent unauthorized access. This ensures that the building remains functional and accessible for its intended purpose while maintaining security measures to control entry and exit points.
About Architectural Planning And Policies
Beyond the CIA Triad, the concept of governance in architecture relates to urban planningand building codes. City planners establish zoning regulations and architects adhere to building codes, contributing to a governance framework that guides the design and construction of structures. This governance ensures that buildings align with safety, environmental, and aesthetic standards.
About User Management
User management in architectural design extends beyond physical access to encompass user experience. In spaces like museums or educational institutions, architects consider the flow of human traffic, ensuring that users can navigate the space efficiently. This user-centric approach enhances the overall experience while mitigating potential congestion and access-related challenges.
About Access Control
Access control in architecture translates to the strategic placement of entrances and exits. Architects design secure entry points with features like key card access, turnstiles, or security personnel to control and monitor access. This physical access control measures mirror their digital counterparts, ensuring that only authorized individuals can enter specific areas.
About Cybersecurity
In modern architecture, the integration of smart building technologies aligns with the concept of network security. Buildings equipped with surveillance cameras, sensors, and automated systems are akin to interconnected networks. Architects must consider cybersecurity measures to protect against unauthorized access to these systems, ensuring the integrity and confidentiality of data.
For more insights into the application of security principles, especially in the context of law enforcement and intelligence, you can read FBI Admitting Informants Joined Charlottesville Riots.
CIA Triad - FAQs
What Is The Concept Of The CIA Triad?
The CIA Triad, an acronym derived from the principles of Confidentiality, Integrity, and Availability, serves as a foundational framework in information security. This triad is not a model in the conventional sense; instead, it represents a set of core principles that guide the design and implementation of secure systems.
Is The CIA Triad A Model Designed?
The CIA Triad is not a model in the traditional sense, but rather a set of guiding principles. It provides a holistic approach to information security by emphasizing the following:
- Confidentiality:Safeguarding sensitive information, ensuring that access is restricted to authorized individuals.
- Integrity:Ensuring the accuracy and reliability of data by preventing unauthorized modifications or alterations.
- Availability:Balancing accessibility for authorized users while preventing disruptions, ensuring data and systems are available when needed.
What Are The Real Life Applications Of CIA Triad?
The principles of the CIA Triad find practical applications in various real-world scenarios, extending beyond the realm of digital information:
Healthcare Systems:
- Confidentiality:Protecting patient records and sensitive medical information from unauthorized access.
- Integrity:Ensuring the accuracy of patient data to prevent errors in medical diagnoses and treatment.
- Availability:Ensuring that healthcare professionals have timely access to patient information for effective care.
Financial Institutions:
- Confidentiality:Safeguarding customer financial data to prevent unauthorized access or identity theft.
- Integrity:Ensuring the accuracy of financial transactions to maintain trust in banking systems.
- Availability:Providing uninterrupted access to online banking services for customers.
Government Organizations:
- Confidentiality:Protecting classified information and national security data from unauthorized access.
- Integrity:Ensuring the accuracy of government records and preventing tampering.
- Availability:Maintaining the availability of critical government services and systems.
Conclusion
The CIA Triad provides architects with a robust framework to design spaces that not only foster innovation but also prioritize security. These fundamental principles serve as a guiding beacon for architects, empowering them to create environments that seamlessly blend cutting-edge design with a resilient security infrastructure. By incorporating the principles of Confidentiality, Integrity, and Availability, architects can navigate the complex landscape of modern design making an impact.
Jump to
Why The Central Intelligence Agency (CIA) Takes Interest In Information Security
The Pitfalls Of Post-Development Security
The Need For A Unified Information Security Architecture
The CIA Triad - Core Principles In Information Security
Beyond The CIA Triad - Additional Considerations
Real-world Applications
CIA Triad - FAQs
Conclusion
Latest Articles
Popular Articles